By Jeremy Wittkop, CTO, InteliSecure
The world is changing quickly, and that is especially true for healthcare organizations. Digital Transformation was already well underway for many organizations, but the events of 2020 have rapidly accelerated those trends, as many are forced to cater to an increasingly remote workforce while trying to control costs.
Healthcare organizations are especially challenged with data protection. If you think about healthcare, there is a good chance several categories of sensitive information exist inside these organizations. Most healthcare companies have significant volumes of Personally Identifiable Information, Personal Health Information, financial information for the purposes of collecting payment, and very valuable Intellectual Property related to drugs, treatments or other research activities.
Cloud services and sharing platforms make it much easier to collaborate with colleagues and customers, but this type of collaboration puts pressure on traditional security models. To keep information safe, the security model must be re-architected to reflect the new reality of how information behaves after digital transformation has begun.
The implication of securing the digital transformation is that traditionally disparate disciplines must converge into a single architecture, or at least be connected via robust APIs (Application Program Interfaces) so they can communicate effectively. Technologies like web gateways, email gateways, Identity and Access Management platforms, Cloud Access Security Brokers, and Data Loss Prevention Systems must work together seamlessly to meet the challenges of the digitally transformed world. The logical place for these integrated technologies to operate is the cloud, rather than a traditional data center. The re-architecture of traditional security infrastructures to integrated cloud-native microservices is no less significant or impactful than digital transformation itself.
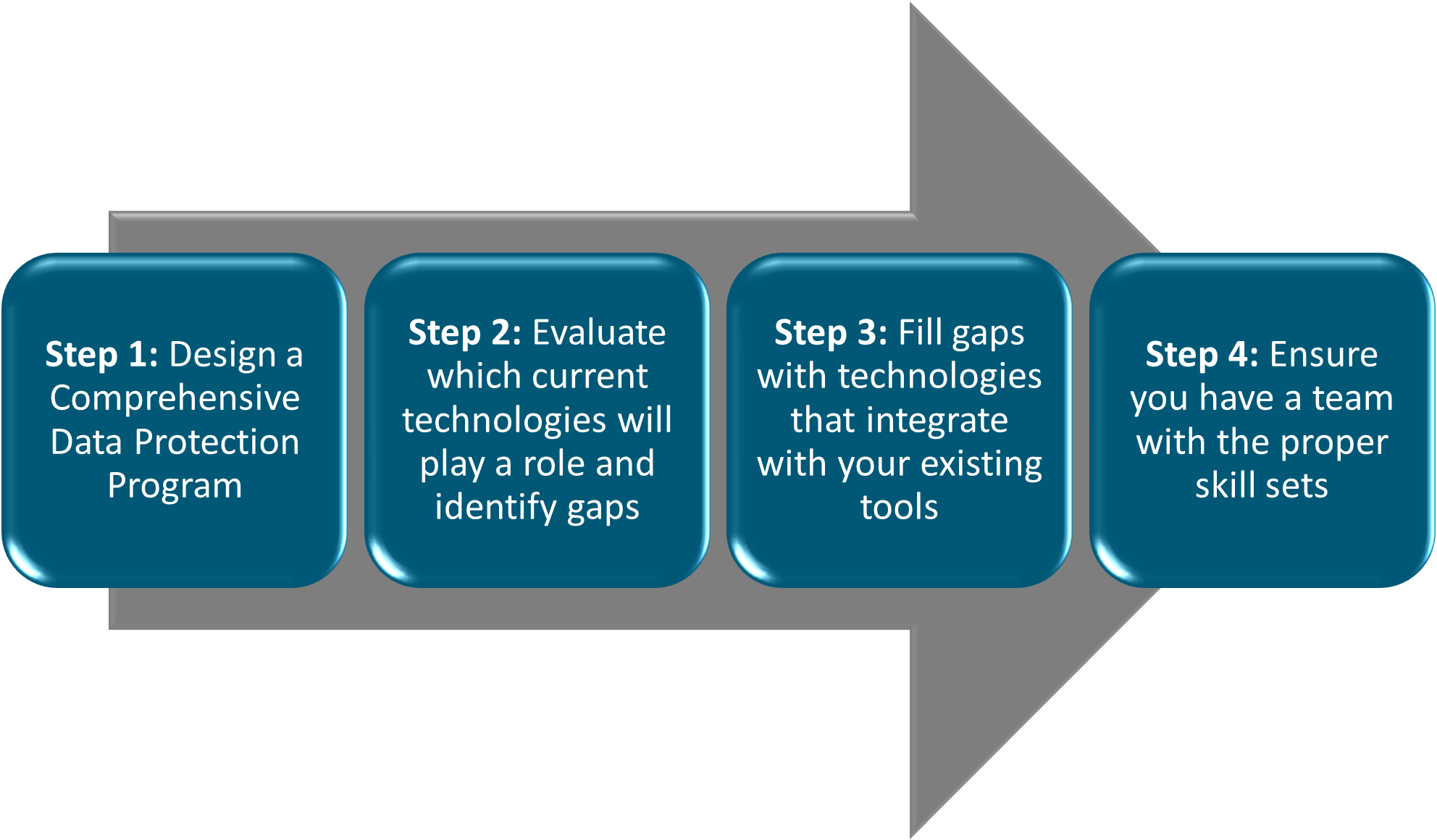
Figure 1: InteliSecure has designed a simple, but effective process to guide clients through the journey of designing an agile security program.
Many people talk about this journey through the lens of technology, but in a converged world, the most important aspect is designing a program. Once the program is designed, the next step is assigning roles and responsibilities to each necessary technology within that program. Think of building a team inside of an organization. If you were to hire a team with skill sets, but some of them overlapped, and you did not give each person a job description with roles and responsibilities, what would happen? You would have organizational chaos. Some tasks would be performed by multiple people with little communication, while others could be missed because people with the skills assume someone else is performing the task. This is how many security programs are designed today, with each technology working in a silo with no comprehensive program to tie them together.
Define the program
The first step is to define the program at the governance level, defining what risks the organization faces to their tangible and intangible assets, and how they intend to treat those risks through the four risk treatment strategies: risk acceptance, risk avoidance, risk transference or risk mitigation. Risks that fall into the risk mitigation portion of the risk treatment plan should be the focus of the security program.
Identify compatible technologies
The next step is technology selection. Most organizations have some security technologies in place, which means that once the program is built, the security team should perform a gap analysis to evaluate which technologies will meet their needs and what gaps exist. When gaps are identified, solutions can be identified that both fill the gaps and seamlessly integrate with existing technologies. The integration evaluation is very important but often overlooked. Success in a digitally transformed world requires technologies that integrate in order to achieve success. Technologies that do not have deep integrations may be cheaper from a price perspective but will cause additional operational costs that often exceed the original savings. Worse, some objectives may not be accomplished at all without a meaningful integration.
Evaluate your team
Finally, the security team must be evaluated. Do you have enough of the right people to effectively manage your technologies, operate your processes and achieve results? If not, you are not alone. The security skills gap is real, and it is growing. There are options available to outsource management of technology to a third party, which can be an attractive option. Alternatively, it is important to proactively recruit and develop security talent. The market for security professionals is strong, so if internal staffing is your strategy, you should be prepared for any member of your team to turn over at any time. Retention should be a focus area, but so should identifying talent that could replace your key team members if one of them should decide to leave the organization.
Most security programs, especially data protection programs, do not fail because the organization does not spend enough money on technology. They fail because they lack the appropriate skill sets in-house to manage the technology appropriately, they failed to build the program first and design effective processes to maximize the value of the technology, or the technologies they selected do not integrate with each other and important events fall through the cracks. Some organizations experience all three.
At InteliSecure we noticed a trend with our clients who utilize the Microsoft ecosystem of security tools. Microsoft E-5 licenses provide several tools with the ability to solve a variety of security challenges. Microsoft also provides a Graph API which allows those tools to integrate. The first step was for us to design their programs so we could prioritize the tools that would have the most material impact on their risk posture. Every time, we found that there were multiple Microsoft tools that had disparate consoles and workflow engines.
Optimization of the programs required us to build a single console, which we named Aperture, to integrate the workflows and events while pulling all information relevant to the program into the console leveraging the Microsoft Graph API. For use cases Microsoft could not solve for our clients, we augmented the solutions with other tools, but a key part of the selection process was seamless integration between Microsoft and the other tools. As a result, organizations can classify information, protect it on premises, in motion through web and email, and in the cloud with a single workflow and overarching policy set. This approach allowed us to build a single dashboard that shows their compliance with HIPAA, CCPA, and PCI along with how their Intellectual Property is moving throughout the environment.
As an example, we work with a healthcare company primarily providing services through hospitals and clinics in the United States. With a single vendor that provides Data Loss Prevention and Cloud Access Security Broker for them, they are able to manage their policies and events in a single console and allow multiple teams to collaborate through the central management platform. They also have Data Classification from a different vendor, but the integration between their vendor and their other supported products means they can manage all three products with a single workflow engine. After obtaining a Microsoft Office 365 E-5 Compliance package, they were directed by their management team to replace their existing tools with Microsoft tools. The security team expressed that by changing platforms, their level of effort would increase significantly. While Microsoft was a single vendor, their workflow would be spread over multiple consoles, and some of their workflow capabilities didn’t exist in the Microsoft ecosystem at all.
When we showed them Aperture, we were able to streamline the security team’s workflows from even their existing processes by consolidating the workflow into Aperture and providing them with useful capabilities that don’t exist in any other data protection platform.
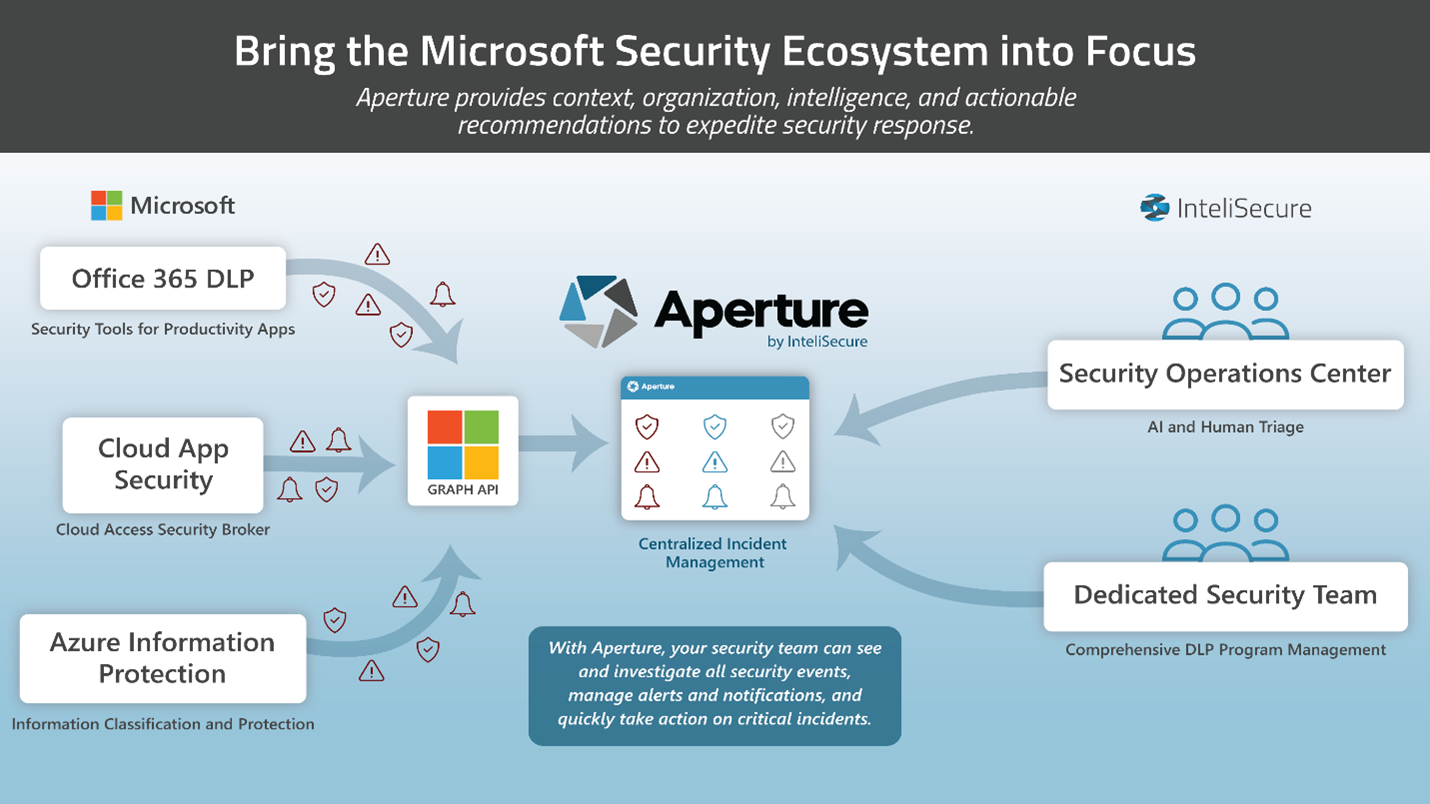
This is simply an example as we have found similar success with a variety of tools. The key is making the people, process, and technology work seamlessly together, and ensuring the technologies can also communicate so each can play their part, but a comprehensive security picture emerges.
Digital transformation is underway inside many healthcare organizations, and the pace of change seems to be accelerating. Additionally, governments around the world have defined digital privacy as a human right for their citizens. The only way for organizations to address the challenges of today while preserving the agility to change with the business is to design a modular program focused on business outcomes. They then can select the technologies that fit best within their program. This makes sense logically, but unfortunately, too many organizations select their technologies first and try to build their program around them as an afterthought.
About the author: Jeremy Wittkop is InteliSecure’s Chief Technology Officer and was a foundational architect for InteliSecure’s internationally recognized Data Protection Managed Security Services, Cloud Security Services, and User and Entity Behavior Analytics Services. Jeremy is a trusted data protection thought leader — published author, blogger, public speaker, and advisor to both clients and private equity investors.











